Cybersecurity is an interesting domain and so are the interviews. Owning to the broad range of topics in the information security domain, identifying the key areas seems challenging. From the perspective of Industry, some concepts definitely need a stronghold to stay firm in this domain. A few questions mentioned below constitute the most frequently asked questions during cybersecurity interviews. Make sure you understand all of the following cyber security interview questions and answers clearly before appearing for your interview to get that job for sure.
Please feel free to leave more cyber security interview questions in the comments and our team will be happy to share the answers.
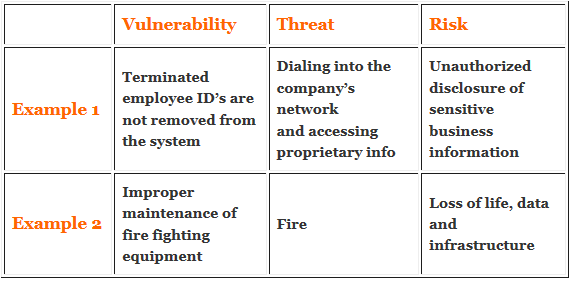
1. What is risk vulnerability and threat. Explain with example


2. What do you understand by a Zero-Day attack?
Zero-day attacks make use of zero-day vulnerabilities. As we are aware, software vendors frequently release security patches to fix known issues and upgrade the security of their products. Sometimes however, there lie vulnerabilities in the products that are either unknown to the vendor or the patchwork is in progress. Such vulnerabilities are called zero-day vulnerabilities. In simple terms, any vulnerability for which a public patch is not available can be referred to as zero-day vulnerability.
Zero Day Initiative is a famous example of websites that publish information about zero-day vulnerabilities.
3. What is SSL and why its important
SSL (Secure Sockets Layer) is a standard security protocol used for establishing an encrypted communication channel between a browser and web server in an online communication.
The advantage of SSL lies in the fact that since the data is encrypted, any attempt to intercept the data may give access to encrypted data only. This results in secure transmission of data including identity information like username, passwords e.t.c.
4. Where do you get your security news?
Its of utmost importance to stay updated in the field of information security. The threat landscape is constantly evolving with new threat vectors getting introduced. Numerous sources for security news are available today. The ones that are followed by me are as follows:
- The Hacker News
- Krebs on Security
- Trend Micro Blog
- Threat Post
- Naked Security
5. Explain phishing and how it can be prevented.
Phishing is a method of trying to gather personal information such as usernames, passwords and credit card details using deceptive e-mails and websites.
Phishing can be prevented and/or the damages can be minimized by adopting advanced technical security measures, specialized trainings, public awareness etc. ‘
6. What do you understand by hashing. Explain
Hashing is a technique for ensuring the integrity of the data, as it helps to ascertain that data has not been modified from its original form. With the use of hashing algorithms like MD5, SHA1, SHA2 amd SHA3, an irreversible fixed length hash value is generated for the provided dataset. This hash value is unique to the supplied input and will drastically change in case of the slightest modification to the supplied input.
Hashing is commonly used in implementing digital signatures and back-end password storage.
Looking for more cyber security interview questions and answers??
- Cyber Security Vulnerability Assessment and Penetration Testing (VAPT) Interview Questions and Answers [Part 1]
- Cyber Security Vulnerability Assessment and Penetration Testing (VAPT) Interview Questions and Answers [Part 2]
- IT Security Risk and Compliance Interview Questions with Answers
- Frequently Asked IoT Security Interview Questions With Answers





Good article and excellent way to articulate, keep it up