With the number of cyber-attacks reaching well above tens of millions on a daily basis, cybersecurity should be at the top of mind for nearly every modern business. Cyber threats are now on the priority agenda for IT departments of organizations of any size and nature. In the case of a cyber incident, the response teams follow the incident handling process defined beforehand. Sophisticated monitoring tools can help to identify a breach before it gets out of hand and advanced diagnostics will assist in classifying the impact of the attack. Well defined incident response techniques help in quick resolution of cyber incidents.
With respect to cyber incident handling, we here present detailed steps that might be used as a one-stop solution for cyber incident handling. The entire process can be categorized into six main steps, each with its further deep digging. The following outline is intended to be a list of steps for dealing with the threats and the compromise accomplished if the threat materializes. However, customized tailoring to each environment and situation is recommended.
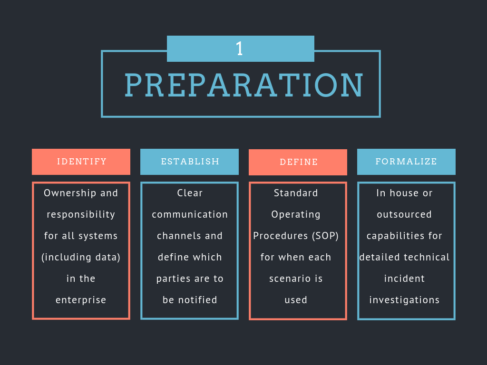
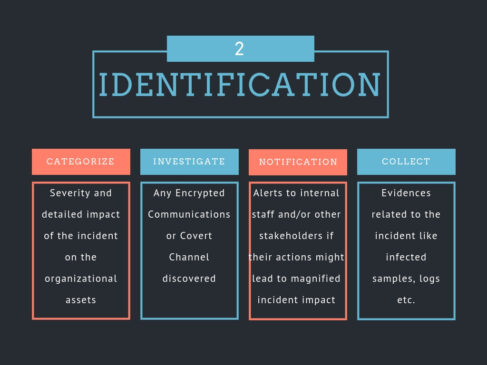
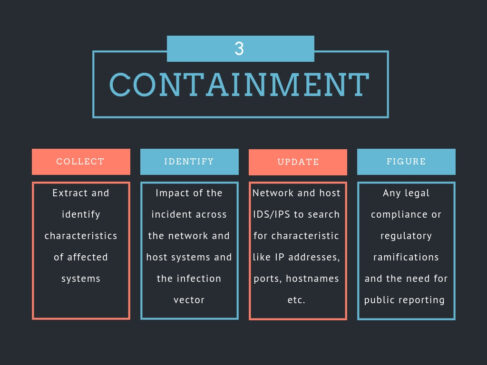
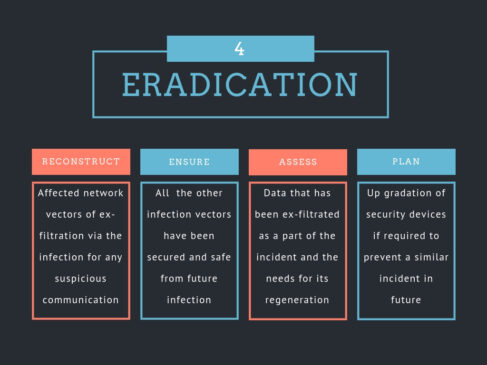
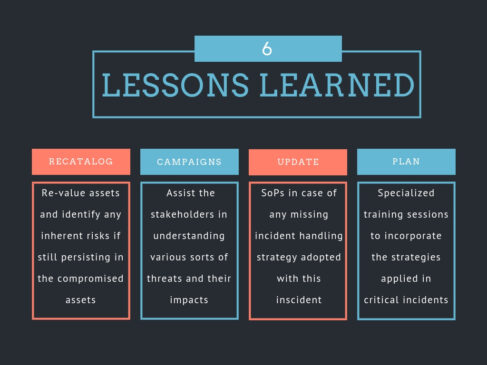
The incident handling process has been categorized into six steps as mentioned in the above figure. The key aspects to be focused on each step is as follows:

Interested in learning more about the cyber incident response process?
Join this amazing Cyber Security Incident Handling and Response course today!